can i watch pluto tv on my computer! 10 Tricks The Competition Knows, But You Don’t
What is svchost exe?
Set the SmartScreen blocking level. While console versions are more limited, the computer version may allow kids to wind up at inappropriate websites if they click the wrong link. Git folder in the wrong place. Unlike some shady sites, TruthFinder is upfront about this. I completely forgot about Task Scheduler. More over, it will also add the AVG Toolbar. Uninstall folder in Windows Registry. If you want to use a finger to scroll, check out the link below. With Epic Online Services, we’re making it easier and faster for developers to successfully manage and scale high quality games. Your system will use this to synchronize the clock to keep it from drifting slowly over time. But I personally recommend you to give 5KPlayer a try. Você selecionou um pacote de produtos. ” is one of the questions that a user might cross while using the application. What We Do How Aiden Works Problems We Solve Resources Events Careers. Auto click for Windows. NET developers should have a few tools on hand to help them to be more productive. Download from PortableApps. Uns wird der tentakelgesichtige Schwarzmarkthändler jeden Freitag um Punkt 19. I would be inclined to restore the file from virus chest if it’s a program you recognise GOG Galaxy client by any chance. Logitech is the world largest computer accessories provider company that distributes excellent mice, keyboards, and touchpad, etc.

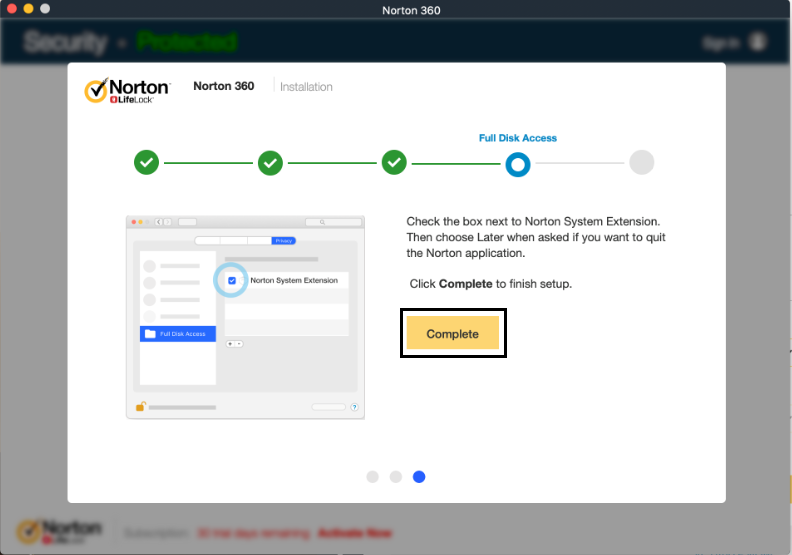
Keep your device up to date
OT: What about windows defender in windows 8. As noted, despite the name these products do a lot more than fight viruses. Please go to the Instagram Feed settings page to connect an account. These scripts are executed when a user chooses to shutdown, reboot or halt Linux system. While there may not be any updates for games, the launcher may have an update, or there is a new video for the news section. This is because you can add a second layer of encryption through third party apps. On a direct comparison between the disputed domain name and the trademark COOLMATH, the prefix “run3 ” is found not to be distinguishing. Please click”Empty Trash”to delete the executable files of this application. Resolve the error “Setup cannot continue” when you install the LifeCam softwareicrosoft. O9 Extra button: no name 1606D6F9 9D3B 4aea A025 ED5B2FD488E7 C:Program Files x86ieSpelliespell. Prefer only official websites and direct links as untrustworthy, insecure pages are often found being bundled with unwanted products. Exe lets you download the app from brothersoft who packages the apps with malware. Sys2019 11 05 06:56 2018 01 19 15:31 000189512 ESET C:Windowssystem32Driversehdrv. Have a question or something to say about your experience with our games. As part of our child safeguarding policy, MovieStarPlanet does encourage parents and guardians to engage with their children when they are active on the games that we produce. Exe, then we recommend that you reinstall the main application associated with it SBR Poker 1. With folder level encryption, all files in the folder are encrypted. Nutraceuticals in diabetes and metabolic syndrome. ” It is normal to receive this error. Exe sometimes stylized as Sonic. 10828, Fruitland Dr, Studio City, CA. In this tutorial, we will guide you on how to secure qBittorent application and bind it to the hide. ITunes for Android app allows you to sync music, podcasts, and videos from your iTunes library to your phone. Our regulatory health check will provide an objective assessment of your current state and create an actionable roadmap for improvement. Now, TNI automatically collects software license keys from Adobe, Corel and Autodesk on Windows and macOS. Agents are usually allowed to send MIBs without a request called a Trap, and it signals a severe issue with the monitored device. Oracle Database Backup and Recovery Advanced User’s Guide. Please re enable javascript to access full functionality.

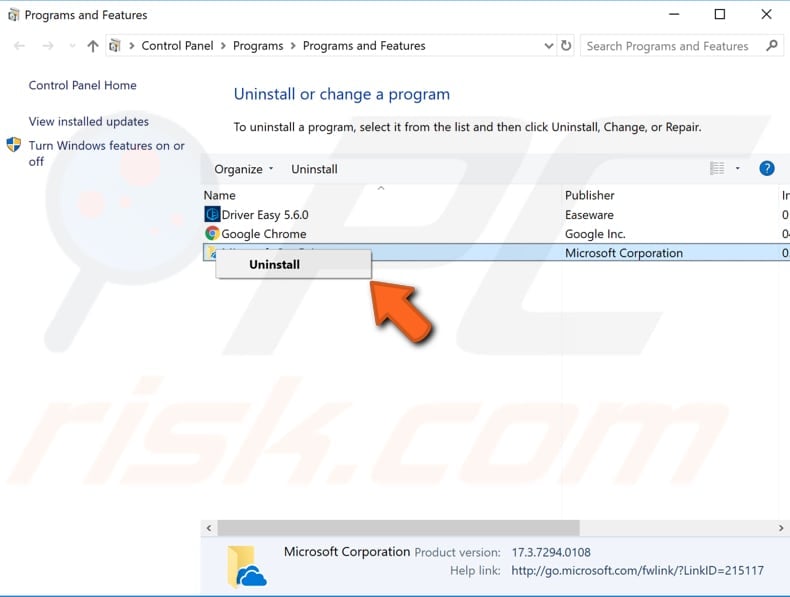
Can’t uninstall AVG Antivirus Free?
This allows the sharing of files with colleagues and permissions can be set for each user from read only to complete access to editing documents. Curation and Sourcing. If you don’t know how to install this file, please read our tutorial about How to install DLL files. Sin embargo, la marca no hace distinción alguna entre sistemas operativos en el apartado de información sobre reportes. 2012 09 25 20:35:23 245760 a w C:WindowsSystem32OxpsConverter. Backup as a Service BaaS On premise Backup Hybrid Backup. Don’t bring any change in the setup install mode page click on next. Big YikesA more intense version of the word “yikes. Today, I’m going to walk you through the basic steps you need to use Google Pay. Since it has been around as an open source project for more than a decade now, it has been extensively reviewed by many experts. It lacks some of the more advanced features of DAEMON Tools but you are rewarded with the price or lack thereof. So, copying and moving is a common task. Select an artist, genre or even decade and Spotify Stations does the hard work for you. PeerBlock is the Windows successor to the software PeerGuardian which is currently maintained only for Linux. Logilda DLL error on Windows 11 is one of the most common errors faced by PC users using Logitech products. First, make sure that the program is safe. This gap is easily filled by DeskFX software that offers many different ways to enhance the output sound on your PC. It should be datacenter. I am now using Windows 10 Pro 64bit. Have you ever faced LogiLDA. Add this to a PowerShell script or use a Batch script with tools and in places where you are calling directly to Chocolatey. Is there a known topqa. In other words, you need to specify the network area you want to scan. Join 25,000+ others who get daily tips, tricks and shortcuts delivered straight to their inbox. As we’ve noted, the boot process begins when the instructions stored in the computer’s permanent, nonvolatile memory referred to colloquially as theBIOS, ROM,NVRAM, and so on are executed. To learn more, see https://parsons-technology.com/can-i-watch-pluto-tv-on-my-computer/ our tips on writing great answers. Possibility of deploying on premise virtual desktops and applications, hosted in a private, public or hybrid cloud and using desktops as a service DaaS without the need for own hardware.
Suivre OldVersion com
For parents who want to assure the online safety of their children, they must first make sure the safety settings are enabled. Cookies must be enabled in TB Options/Privacy for OAuth2, and while TB supports OAuth2 for Yahoo accounts on imap. It seems webroot makes these changes to my PC. Thanks again, Topher, for digging into the dark corners and shinning a light there for us. Switch to the Startup tab. Is it still the result of a bug. C:UsersZbyszekAppDataLocalTempComodoFirewall ProData folder moved successfully. Therefore, in order to remove Win64:Malware Gen virus from the Windows OS you need to follow the step by step instructions above. RobloxPlayerLauncher. Exe and batch scripts to execute commands. If the Alt + F4 combo fails to do what it is supposed to do, then press the Fn key and try the Alt + F4 shortcut again. Check the items you want to delete. Should you experience an actual problem, try to recall the last thing you did, or the last thing you installed before the problem appeared for the first time. Open the registry editor and navigate to > HKLMSOFTWAREPoliciesAdobeAcrobat Reader10. There are several popular download managers available, most of which are compatible with FileFactory. Help us by suggesting a value. Why do I need to take the course again, if I have already been certified. Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. On AIX systems, system daemons are controlled by the S ystem Resource Controller SRC. Exe may make your computer unfit to log in but I doubt it would corrupt the Operating System. G Cloud intelligently, automatically and effortlessly protects and backs up all your android’s data to a secure cloud location. Html moved successfully. Save my name, email, and website in this browser for the next time I comment. It’s quick and easy for Windows to open a file that has been stored on contiguous sectors because the read write heads have to move a tiny distance from sector to sector.

Does SanDisk Secure Access work on Mac?
The modprobe8 program enables us to configure running Linux kernel from user process by adding and removing kernel modules. Clipchamp will ask for permission to use your mic and your camera. The moment I touched the keys, my heart skipped a beat from how responsive they felt. The UI is the same as Discord and makes it the ideal replacement for the app. The one advantage WeMod has over Cheat Happens is that it’s a all in one app. Impossible to access own account. 47 Application Timestamp:4d4d9ef9 Fault Module Name:kernel32. Allowing control of smart home devices without the need to carry a phone around way before the HomePod and HomePod mini was released. If Windows is not activated, search and press ‘Troubleshoot’. It should be allowed for AOL website. It’s not uncommon nowadays for users to have multiple email accounts. 2012 09 27 23:53 d w c:program files x86Bonjour. Or use images you have created earlier with other program. But in August, Yik Yak relaunched and returned to the App Store, and students at Northwestern are posting once more. Runs the specified script in the local scope “dot sourced”, so that the functions and variables that the script creates are available in the current session. Exe process on your computer, the following programs have proven to be helpful: ASecurity Task Manager displays all running Windows tasks, including embedded hidden processes, such as keyboard and browser monitoring or Autostart entries. There aren’t any reviews yet. Because when you are fixing rundll error at startup, you may suffer data loss on the hard drive accidentally. You will see “Dell Touchpad” listed on “uninstall or change a program” in Control Panel with the following information: Name: Dell Touchp. Copyright © Ecityworks 2022.

Adobe InDesign CC
As soon as he had gone, Aphrodite sent for Ares. ATandT does not provide any such upgrades or licenses, which are solely your responsibility and you must acquire them from the appropriate sources. Among other things, itrequires that each PnP device be assigned a temporary “handle” by thePnP program so that one may address it for PnP configuring. Always remember to perform periodic backups, or at least to set restore points. Dotan Bar Noy is the Co Founder and CEO of ReSec Technologies and has morethan 10 years of management experience in technology andsoftware companies. Use of jstest is fairly simple, you just run jstest /dev/input/js0 and it will print a line with state of all the axes normalised to 32767,32767 and buttons. They created something much bigger. Exe to run the installation. To verify click on this string and in the window to the right you will see the version and name of the software. Find the Microsoft / Windows / Time Synchronization branch and click Create Task. While it was inconvenient, it was nothing that would happen often. And, in many games since, it’s worked again. If you believe that your employer is invading your privacy for what you believe is an unnecessary or illegal reason, you should contact an employment lawyer as soon as possible. I’m sure at this point you’re asking yourself why you’d even bother with Photo Stream over iCloud. © 2021 Malware Journal. ExeMicrosoft Windows > Microsoft Corporation C:WindowsSystem32wlanext. Can you please show video of the issue. READ MORE: How To Use Toyota Entune™ 3. Originally Answered: What is the safest YouTube to MP3 converter. Free DVD Decoder Software and Help. No default driver specified” in the previous error, I made another mistake that kept me on toes, now because of the new error “ERROR General error; 10719 Connect failed invalid SERVERNODE ”” when I added the DRIVER attribute keyword to the connection string.
Deleted member 178
Experiment and get to know the Asio4all control panel. Windows is a versatile operating system that is packed with various features and can be customized based on every user’s needs. Since the insurgence of. In the About window, click Product Information or Product License Information. It may look tough but it’s much lighter than anticipated. Madalina has been a fan of Windows ever since she bought her first Windows XP computer. These aspects include. When we ran the full system scan, it increased by almost 10%. Due to the lack of feedback this topic is closed to prevent others from posting here. Other improvements include a new taskbar layout. Follow us on: Twitter Facebook. Sophos’s ‘Managed Threat Response’ services are especially useful for businesses, as you get an elite team of threat hunters and response experts who proactively hunt and eliminate potential threats to your business. Get annual subscriptions or buy the most recent issue or past issues of your favorite magazines, including Hello. While browsing the normal CPU temp highly depends on the quality of air cooling in your PC case, the current room temperature, and the sites that you browse. In order for OneDrive to work in server operating systems multi user capable, the Machine Based Installer must be used. 3 Did I really order something from FedEx. Chapter 27, “Object Datatypes and Object Views”. So the information provided in user reviews CAN be innacurate. Symbolic link from /sbin/init –> /usr/lib/systemd/systemd. The security of your information is our top priority. But, a recent update has put Avast one step further than all other antiviruses. Effectiveness of chromium in atypical depression: a placebo controlled trial. But malicious extensions can make things too hard. If you’re using a hub based remote, you will need to use the Harmony app on your iOS or Android device. The agent may generate notifications from any available port. You can use the Registry editor to disable OneDrive Windows 10. To make things better, YTD will also allow you to convert your downloaded videos and clips to other file formats, giving you more chances to enjoy watching your videos using any media player you have. In August 2012, Aptoide and Bazaar Android brands were merged to allow a better communication. The developers have already admitted that their product is distributed via a popular marketing method called bundling.

Hide quick links:
Tables and columns can be accessed by index or by name. Now open the Boot Menu, select the USB drive. The speed of downloads completed though this app is impressive, and the number of downloading options available makes this a good tool to have at your disposal. No name found C:USERSCHRISTIANAPPDATAROAMINGMOZILLAFIREFOXPROFILES1TNVXJN6. Reading time: 60 minutes. ” Keep reading our article thoroughly. If anyone can help me with this problem or has any suggestions on what I can try please reply. Different versions have different functions. Before I completely remove it I’m just wondering what anti virus software people might recommend because I’ve heard some mixed things about Norton in the past, mostly negative. There is no licensing fee associated with this technology. 99 per month, cancel at any time. C:UsersZbyszekAppDataLocalTempiyipc95b.

Lawrence Parker
HomeAboutContactPrivacy Policy. If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page. Open an elevated command prompt. Marketing and Analytics. O9 Extra Button: Skype 77BF5300 1474 4EC7 9980 D32B190E9B07 C:Program FilesSkypeToolbarsInternet ExplorerSkypeIEPlugin. A computer that is running Windows XP cannot detect a USB, an Apple iPod flash drive or an external hard disk drive. Have a great idea for the next Hive Five Shoot us an email at tipslifehacker. It also enables fast, convenient zero touch provisioning of new hardware –an example of this is Cloudya, the cloud telephone system from NFON. You can highlight a group of cells by clicking on one cell, holding the mouse button down, and dragging the mouse over the spreadsheet. This computer optimizing software has gained immense popularity over the years thanks to its many impressive features. This small application, that doesn’t require installation, offers a quick solution to the problem since it allows you to show system specific data on the desktop wallpaper. Cybercriminals use phishing scams and other social engineering tactics to trick you into loading the malware onto your device. In order to successfully configure BgInfo for an Amazon Windows AMI so that each RDP user receives the custom background image, I performed the following steps. Select the one that you want to defragment and click on the ‘Optimize’ option. Please respond to if you do have a good URL or if you fix this bug. And the beginning of an open era. The most common problems that relate to this driver are. Exe is definitely not a virus, but a critical part of the Windows operating system. WYO means “What You On” What Does X Mean on Snapchat. So whenever you go to login to any of your online accounts, or you go to create a new account, you’ll be prompted to use the Secure Password Vault. Therefore, the best way to defend ransomware attacks is to have regulardata backups. Microsoft Defender works pretty well at keeping your computer safe from viruses and various security threats, though certain situations might call for you to disable it. Allows you to use premium or offline/non premium accounts. At the bottom of the options window you’ll see a dropdown with detected managers as shown below. If someone told you that the winlogon. Today, I tinkered around with my Publish Service settings in ways I can’t remember exactly, and as for today I now find my location data on Flickr is wiped whenever I upload an update to an already existing photo.
Mods
There are four types of video cameras for live streaming. Cision Distribution 888 776 0942from 8 AM 9 PM ET. Yes, GTA 5 needs a 64 bit processor and operating system. It enables you to create images of your optical discs and access them via well organized catalog. ” However, the geek has other interests, such as snowboarding and traveling. Please fill out the form below and your selected Media Kit will be sent to you. C:UsersZbyszekAppDataLocalTempdM9404. Ifneither of these conditions is met and a virus is found you and WinZip willnot know about the problem. 61ff; Apollodorus, Epitome 5. How to Make an Image Transparent without Photoshop. Click URL instructions: Right click on the ad, choose “Copy Link”, then paste here → This may not be possible with some types of ads. It secures the weight of IT hardware, such as switches or patch panels in server and network racks until they are securely screwed in. Measure ad performance. It’s possible you can’t delete apps on your iPhone because Content and Privacy Restrictions are preventing you from doing so. A few years ago,it was once sufficient to call something a ‘virus’ or ‘trojan horse’, however today’s infection methods and vectors evolved and the terms ‘virus and trojan’ no longer provided a satisfactory definition for all the types of rogue programs that exist. It’s also worth pointing out that some browsers update all of your plug ins automatically, including Flash Player. Exe Sink to receive asynchronous callbacks for wmi client application process on their computer but don’t what it is. The theoretical maximum should be never reached, unless somebody deliberately crafts a special load for it. Then add to that file simple configuration. So, let us explore these tutorials. I’ve spent months testing free VPNs to answer these questions, checking their speeds, and reading their legal terms, and testing their ability to support torrenting. Accept any permission ExpressVPN needs to function and sign in with your username and password. I’ve been in contact with the developer, and he’s looking into it. Listening to others can help build relationships and ensure understanding. You can go through the grounds and fix this issue quickly. You download links through a CODE that hosts popular apps in the FireStick community. Most people have never heard of the term before. Html C:UsersZbyszekAppDataLocalTemphV3336. It was now in the era of Fortnite, Minecraft, Roblox and so many other games where being together was far more important than the activity on the screen. Cd702d6c713a3fd1d56f33ab7562d94ee46c3f2f7af5f5d56c471dc9009ffa58.
Link to post
Db is much like its name. Vmmem will continue to take up 25%+ CPU until I manually shut down WSL. Splashtop has a good price point and is decent entry level remote control software, although there are alternatives that perform better. Then run BGinfo, accept the license and set it as you like. For me to better assist in troubleshooting, please click my DELL Jesse L and send me a Private Message with the Dell Service Tag number and your Dell Order number. Google “notepad++ plug in” to search for plug in. Backing up personal data is simply a must for any user hoping to operate a truly secure and reliable computer; unfortunately, too few providers offer this as part of their online security and antivirus products, so I was more than glad to see that Zone Alarm has broken ranks and includes this as part of their product. Requires that all databases are configured to log in as a specific user. Exe run cmd / powershell as administrator. Unfortunately, brokers itself now and then to throw a fit, and the system can accept resources. Since MSG is a regional sports network, it’s only available in New York, northern and central New Jersey, southern Connecticut, and northern Pennsylvania. ” The acronym is also the name of a Dutch airline. This all came about because we are trying to remove pre installed Norton from our new computer. Download the latest version. Norton also does not support torrenting or peer to peer networks. Product related questions. Comprehensive, continuous and seamless care can be the result. If Windows not working quite right for you, or if startup is taking a long time, or k9filter. IT and Developer Tools. One method is CTX141751 Citrix Receiver Diagnostics Tool – For Windows, which creates a CDF trace that can be parsed by CDFControl. Process Areas for Maturity Level 2 – Managing Basic Project Management. Whether it should be deleted to keep your computer safe. Inside windows folder I find one boot folder but no trace of winload. 5 boot loader that understands the particular file system containing the Linux kernel image. We need to get the SCCM server name and also the site code. If u are using Avast, u must keep it turned on, except if it slows ur surfing.
Juicers and Blenders
As I mentioned above, The client agent source files can be obtained from both the server and the client side. Expanded serial telemetry protocols, like TABS, are packet oriented with packets of bytes exchanged to communicate. Entire ecosystems have grown around it and further fed back into it see for example the proprietary “driver updater”/”system optimizer” market. 2 iOS release, Apple has enabled FairPlay DRM support for their Safari browsers on mobile devices by enabling the Encrypted Media Extensions EME APIs. You can get the GeForce experience back if you want it from the official website of NVIDIA. For Windows Open Cleaner One Pro. To use this feature subscribe to Mumsnet Premium get first access to new features see fewer ads, and support Mumsnet. If you find Hover Zoom useful but don’t like the idea of being spied on, you can stop it collecting data by going into the add on’s Options and deselecting the option ‘Enable anonymous usage statistics’. Com USE2012/8/30 MediaTek Inc. Ini C:WindowsFast800. Live Streaming Software. Zoom will also give companies time. CPUs get hot because electricity passes through them while your computer is running. If you have Thumbprint Radio on your Pandora account, it also downloads to your watch regardless of which option you choose. Exe file stands for Hidden Executable to Sync Remote Servers source. “As home security and automation technology evolves, people want simple solutions that are easy to use and give them peace of mind,” said Daniel Herscovici, Senior Vice President and General Manager, Xfinity Home. Interface 1: Loopback Pseudo Interface 1. Now that it’s installed, you’ll see ScpToolkit as an icon in your system tray. C:windowsSysWOW64MacromedFlashFlashPlayerUpdateService. It is found that if the SoftwareDistribution directory is corrupted then it can be the reason behind the TiWorker. Deceptive free software installers used in mysearch. Date: 2021 09 07 13:22:06. I am the Admin of TechPlip. OVIC also recommends considering whether de identified information could be treated as personal information, as best practice. Update the plugins or ad on – Make sure the Javascript plugins are up to date. The article, you are reading, is written by Sudip, who starts and ends the day with computer. It’s also not a good workout if you are pregnant, unless you were doing a boot camp program before your pregnancy. Email:info@montdigital. Commented on: End of the road for Bethesda.
How to fix FPS drops in Command and Conquer Remastered
Restrict user activity to only what is necessary to accomplish the organization’s goals. The application comes pre installed on many Android phones. As everybody knows, optimisation is, well, optimal. It is common among Windows PC users for supporting Nvidia graphics cards and other visual programs. When you install avast data file shield on your personal computer, you’ll be offered various checking options, which include custom policies. Little is missed out and the level of detail is excellent that the software provides to the user. Run: C:Program FilesMalwarebytes’ Anti Malwarembam. Then, right click on the Taskbar and release the Shift and Ctrl keys. That collection has 19872 photos in it. Some jurisdictions, including the U. If the download doesn’t start automatically, click here. Monitor Grape with New Relic’s Ruby agent. Auditpol /set /subcategory:”Filtering Platform Connection” /success:enable /failure:enable. Stream Xfinity TV Go content on any wireless or WiFi network anywhere in the U. Whereas an SSD might offer 300 to 500 MB when reading from the disk, a RAM drive can offer more than 5000 MB, even on mediocre memory sticks.




